HOW DO PHISHING ATTACKS WORK?
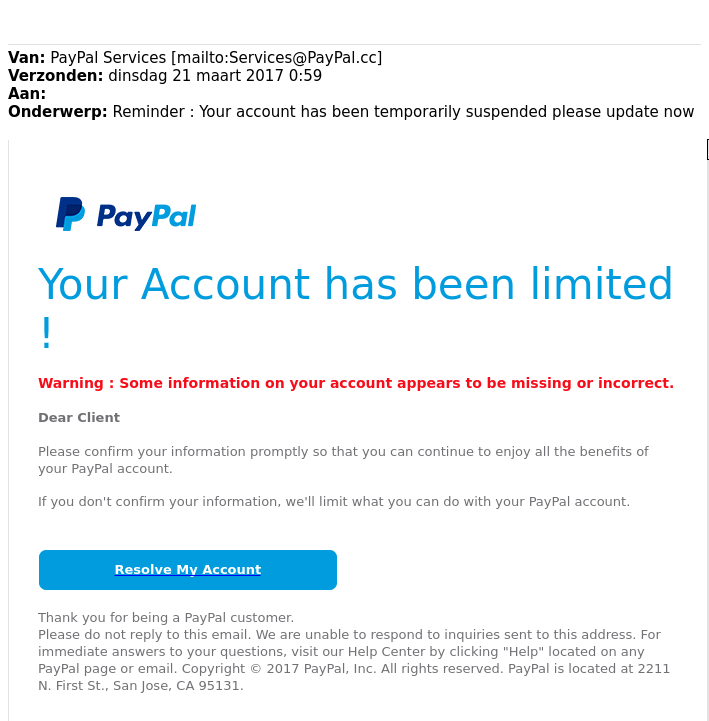
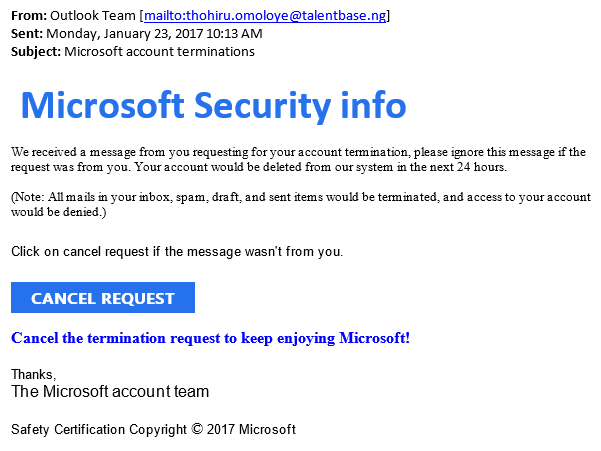
The purpose of a phishing email is to gain access to your personal information and your company’s network, by tricking you to click a link, download an attachment, or login to a fraudulent website which will grant the attackers access to your computer, or smartphone.
1.) CONFIRM WHO SENT IT
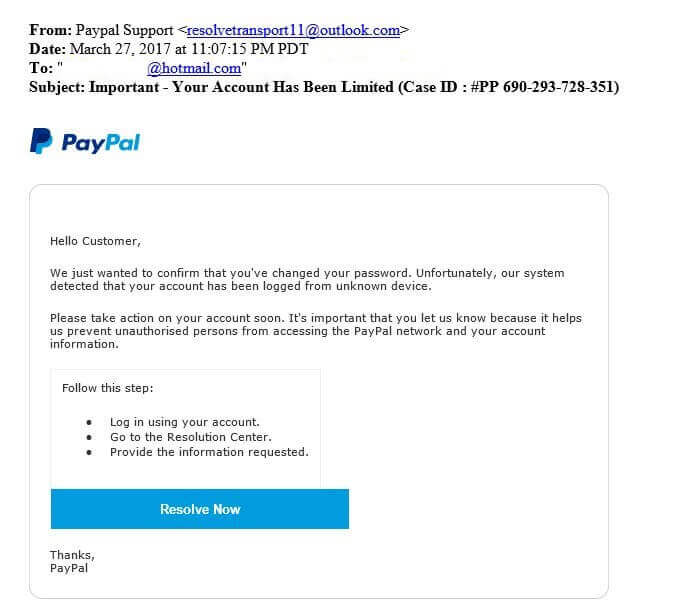
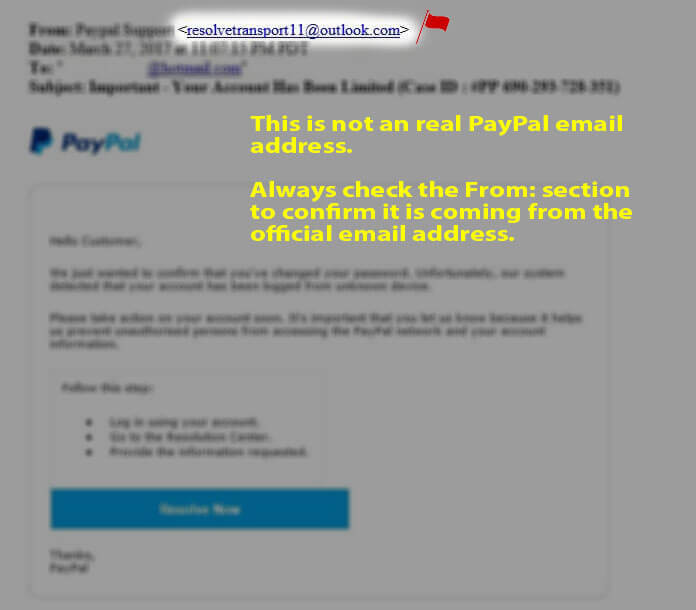
2.) DON’T MAKE QUICK DECISIONS
3.) CHECK THE WORDING
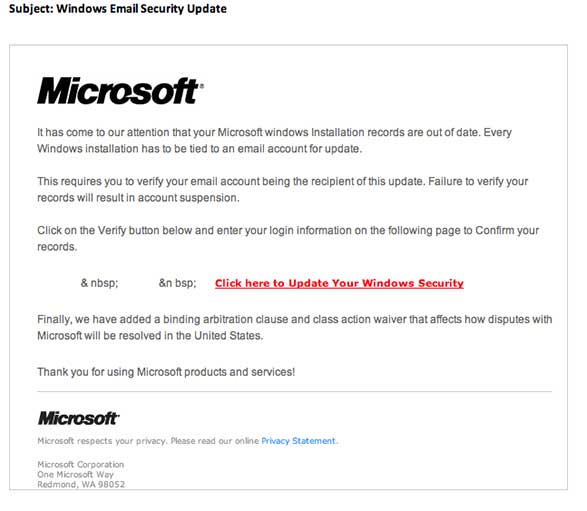
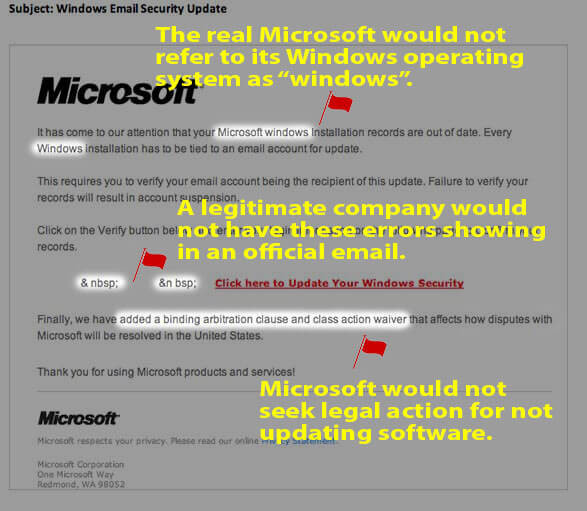
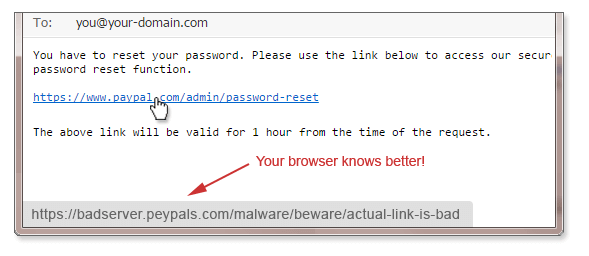
4.) CHECK LINKS BEFORE YOU CLICK
paypal.com.co.ru, or support-apple.io, when you are expecting the official address of a trusted entity. These unofficial websites are usually designed to trick you into providing cyber criminals with your login information, or secretly download malware onto your device.
When in doubt, it is always best to go to the official website directly, or by using a search engine.
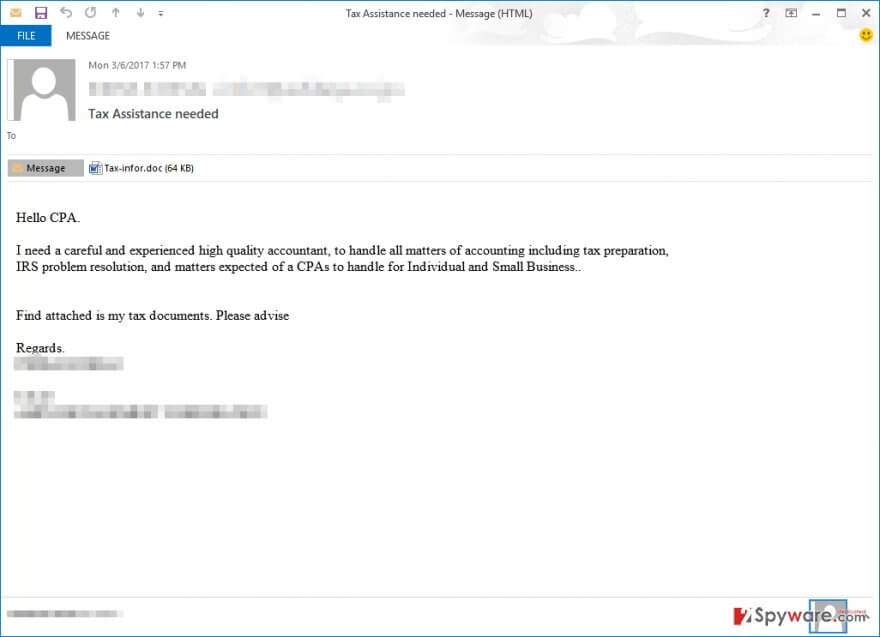
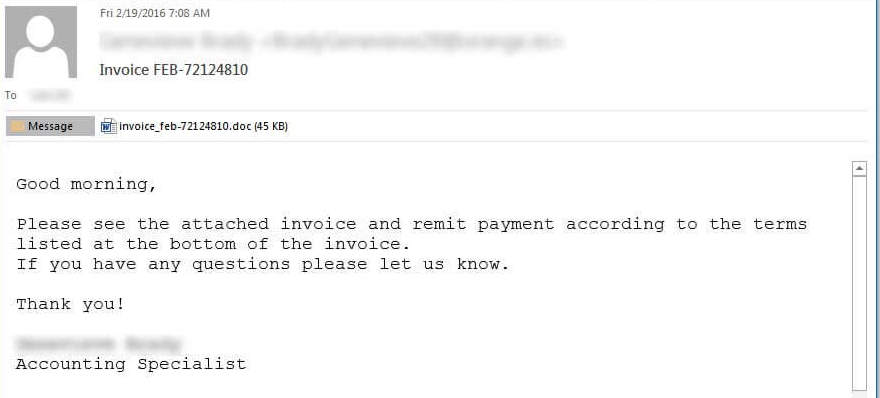
5.) BEWARE OF ATTACHMENTS
Phishing and Malware Prevention
As an experienced IT service provider and consultancy, we can provide expert deployment of anti-malware and anti-spam solutions to prevent you and your employees falling victim to cybercriminals who look to steal your proprietary information and disrupt your business.